Cloud Infrastructure Security Testing
Cloud computing is the new black in the whole IT industry. The data is unambiguous – according to the Cloud Security Alliance, over 98% of businesses use public cloud infrastructure for their operations. At Securing, we believe that cloud security is paramount for all organizations aiming to fully benefit form cloud computing without the risk of data breaches or compromising critical operations.

Having that in mind, our experts can ensure the security of your cloud infrastructure for any of the major providers—AWS, Azure, and Google Cloud—through the following services:
Cloud configuration security assessment
This might come as a shock, but cloud is NOT secure by default. It is crucial to understand that cloud service consumers (CSCs) have responsibilities. Some security controls – depending on the infrastructure model in use – need to be managed by them under the Cloud Shared Responsibility Model:
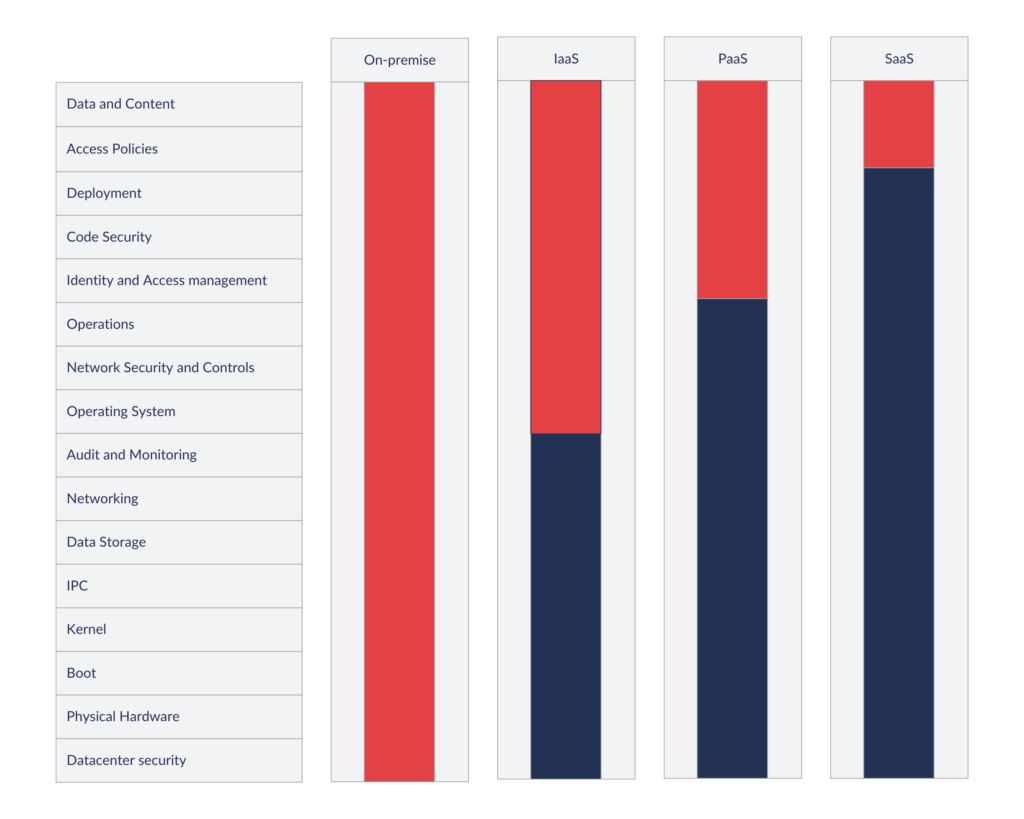
Moreover, the cloud is an immensely complex concept, making it impossible to define a single perfect and secure default configuration that works for all use cases. This is why security configurations sometimes should not remain at their default settings – they must be tailored for the unique needs of your specific cloud infrastructure.
Connect with our Cloud Security Experts!

Our team of experts, with vast experience in the three major public cloud providers, will evaluate the security of your cloud infrastructure. We will identify and report any misconfiguration that could compromise your data or disrupting IT operations. Additionally, we will verify your cloud infrastructure compliance with best practices defined for each platform.

Threat modeling for cloud infrastructure
Threat modeling sessions address three crucial security questions:
- Who?
- What?
- How?
Our specialist will help you identify critical assets within your cloud infrastructure. Together, we will conduct a brainstorming session to develop a comprehensive list of threats applicable to your cloud infrastructure. You will receive a detailed report verified by our experts that includes recommendations for implementing specific security measures.

Penetration testing of services deployed in the cloud environment
Cloud-based application security testing combines our expertise in application security testing with the specialized knowledge of our cloud security team. We extend “classic” penetration testing by incorporating cloud-specific attack scenarios, such as:
- Identifying cloud access tokens or secrets in client applications and attempting to escalate privileges within the cloud,
- Attempting to breach cloud security with web application vulnerabilities (e.g., stealing access tokens through metadata access initiated by SSRF vulnerability),
- Identifying and exploiting overexposed cloud resources.

DORA compliance

Cloud Infrastructure Security Testing contributes to compliance with DORA principles. It aligns with DORA’s relevance to modern cloud-based DevOps environments.
Get a quote for your project
Book a call or fill out our contact form to get a quote for a Cloud Infrastructure Security Testing. Every organization is different – if necessary, we’ll get in touch with you to determine the specifics of your needs and the broader context of security testing.






