Web application testing

Web application penetration testing is a security evaluation process designed to ensure your application, users, and their data are protected. It allows us to identify vulnerabilities that could allow unauthorized access to your data. This systematic approach provides actionable insights into your application’s security posture, helping to prevent real-world attacks.
Connect with our Web App Security Expert!

Why is web application testing necessary?
- Web applications are everywhere these days, regardless of a company’s size, and they are more embedded in our lives than ever before. Because they often hold mission-critical assets (such as data, money, or sensitive information), they are a lucrative target for attackers.
- The expected level of security increases with awareness among both governments and end-users. Verification of a web application’s security posture is often required to fulfill regulatory requirements and build trust among users, with more regulations expected in the future.
- It’s better to catch bugs early in the development process, when they are relatively easy to handle. Fixing bugs in production or after an incident has already happened is usually a whole different story, much more grim and costly.
What does the web application security testing process look like?
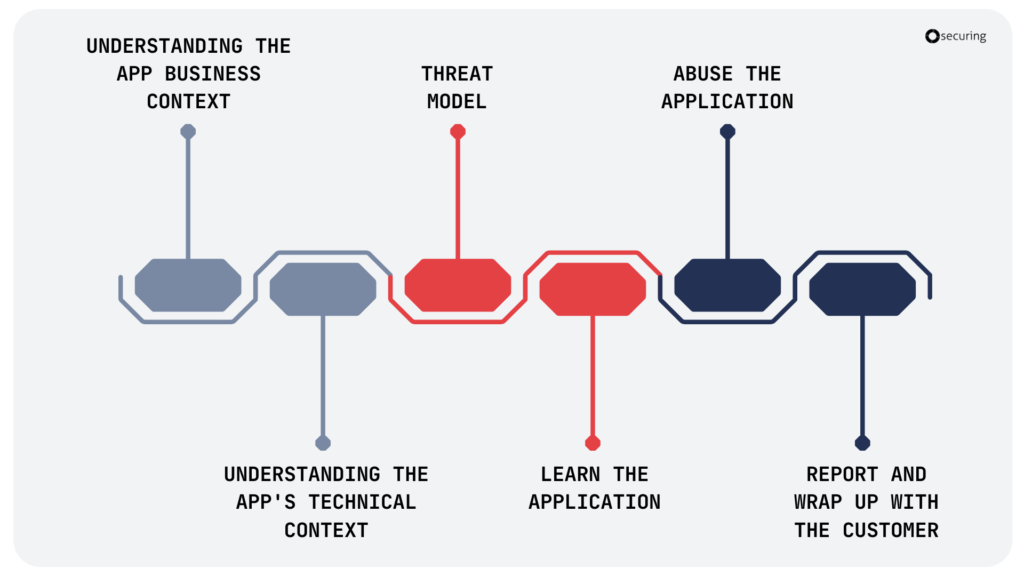
- Understanding the app business context:
- Business model,
- Business processes,
- Actors in the application.
- Understanding the app’s technical context
- Architecture – web servers, cache, load balancers, API gateways, queues, databases, etc.
- Technology stack – framework, languages, frontend, and backend alike,
- Infrastructure – on-prem/cloud Windows/Linux, etc.
- Threat model:
- With the customer at the kick-off meeting,
- Internal – testing team only,
- Prepare an application-specific list of test scenarios and test cases,
- Without this, it’s just blind vulnerability shooting without good prioritization of tests.
- Learn the application
- Use it like a regular user,
- Ask additional business questions.
- Abuse the application
- Use it like an attacker,
- Follow the baseline (checklists, etc.) – execute typical web application security test scenarios and test cases,
- Execute application-specific test scenarios and test cases to ensure optimal performance.
- Report and wrap up with the customer
- Discuss issues and proposed remediations,
- Adjust remediations to the client’s suggestions.
How do we test web applications?

Manual testing
We thrive on manual testing. When a project begins, we assemble a team of individuals with diverse skill sets to assess the application thoroughly.
We carefully watch how the application communicates with the API, what assets it uses, and how the frontend is built. Based on our experience, we pinpoint suspicious points of entry. We also map processes step-by-step and try to abuse the business logic, which is crucial, especially in financial processes. We look for both low-hanging fruit and state-of-the-art crazy stuff, based on the given attacker profile and key threats.
Automated testing
Using just the tools is like riding a car in a place where you should be walking slowly and paying attention to the details of your surroundings. But a car can get you to the destination faster.
We use automated tools to save time on the basics and to improve coverage. We understand those tools and know that the outcome is reliable, so we also verify it manually.
We automate what makes sense to automate, such as enumerations (files, paths, etc.), known CVE scans, and the exploitation of discovered issues, sometimes crafting scripts or extensions on the fly.
As much as we love exploiting SQL injections by hand, time is usually our enemy, and we want to find as many issues as possible. Time saved is spent manually searching for vulnerabilities that align with key threats identified specifically for the tested application.
Collaboration
We are not the type of company that goes silent during the engagement, just sending two emails (one when we start and a second one with the report).

It’s important to be on the same channel as the application team, such as Slack or Teams. We ask questions to understand and show what does not work as expected. We explain what we do and teach about what we consider important.
We help design and securely implement remediations, and we recommend the next steps during the test. We are also keen on learning, understanding why something is done in a certain way and not another, and what the pros and cons of a given code piece or module are. It makes us better at what we do, seeing the applications team’s perspective.
Expertise
We rely heavily on industry standards (OWASP projects, RFCs, Hacktricks), as well as our over 20 years of experience and a culture of knowledge sharing. This experience is built on a strong foundation:
- thousands of penetration tests delivered,
- security research presented at major security conferences around the world.
Our in-house checklists cover all popular technologies and frameworks, ensuring a reproducible set of test cases.
Team
We are a diverse bunch of people with various backgrounds. We are ex software developers, formed administrators, CTF players, ex software testers, and former SOC operators.

We are quality enthusiasts and put a lot of effort into staying up to date with the current landscape of application security, technologies, frameworks, trends, and threats. We share our knowledge both internally and at various conferences, our blog, and LinkedIn.
Just share some details about your application and infrastructure, and we will assemble a team with the right mix of skills and experience to seamlessly integrate with your own staff. Our team becomes an extension of yours, collaborating closely and adapting to your unique needs and workflows. If any unexpected challenges arise, we can immediately bring in specialized experts with deep knowledge in areas like cloud security, system architecture, or mobile apps, ensuring you always have the right expertise at hand.
Industries we are highly specialized in
Industries we’ve also supported include:
- Insurance
- Healthcare & MedTech
- Cloud platforms
- AI-driven solutions
- Government & public sector
- Startups & scaleups
- Aerospace & space industry
- Manufacturing & heavy industry
- Telecommunications
- Retail & e-commerce
- Logistics & transportation
- Energy & utilities
Whether it’s a complex grey-hair challenge, a never-done-before idea, or a mission-critical system – we’ve got you covered. Our team combines researchers, ethical hackers, and international speakers trusted on world stages. Whatever you bring us, we’ll make it secure.
DORA compliance

Web application testing can contribute to the compliance with DORA principles. It aligns with DORA’s focus on securing software components.
Get a quote for your project

Book a call or fill out our contact form to get a quote for Web app security testing. Every organization is different – we’ll get in touch with you to determine the specifics of your needs and the broader context of security testing.




