Security Code Review

In today’s environment, businesses share a huge burden and responsibility to secure data they process through web applications and APIs. What has come with digital transformation requires special care to remain reliable, continuously improve, and ensure its security.
To find the most impacting vulnerabilities as efficiently as possible, we propose a white-box approach to security, offering code reviews that do not overload your development team.
What is a security code review?
Security code review is a process designed to identify security flaws in systems. It ensures that the right security and logical controls are in place, work as intended, and are used in the right places. It does not assess compliance with internal coding guidelines that may be a part of existing peer code reviews. Instead, the focus is solely on identifying exploitable security issues that pose a risk to organizations.
Our approach to security code review
We treat the security code review as a complement to penetration testing and a method of identifying security flaws in your code. It has the following characteristics:
Every security code review consists of automated and manual parts. The former allows us to quickly cover a large volume of code, establish a baseline level of security and a starting point for further exploration. Issues identified at this point are reviewed by a human operator who understands the nature of the vulnerabilities and the context of the system. Context is also the cornerstone of the manual security code review process. It enables accurate risk assessment and categorization, which helps in deciding what to fix first.
We have experience with most major programming languages (C#, Java, PHP, Python, Golang, JavaScript, Haskell, Scala, Objective-C, Swift, etc.). However, do not hesitate to ask for security code reviews of less common technologies!
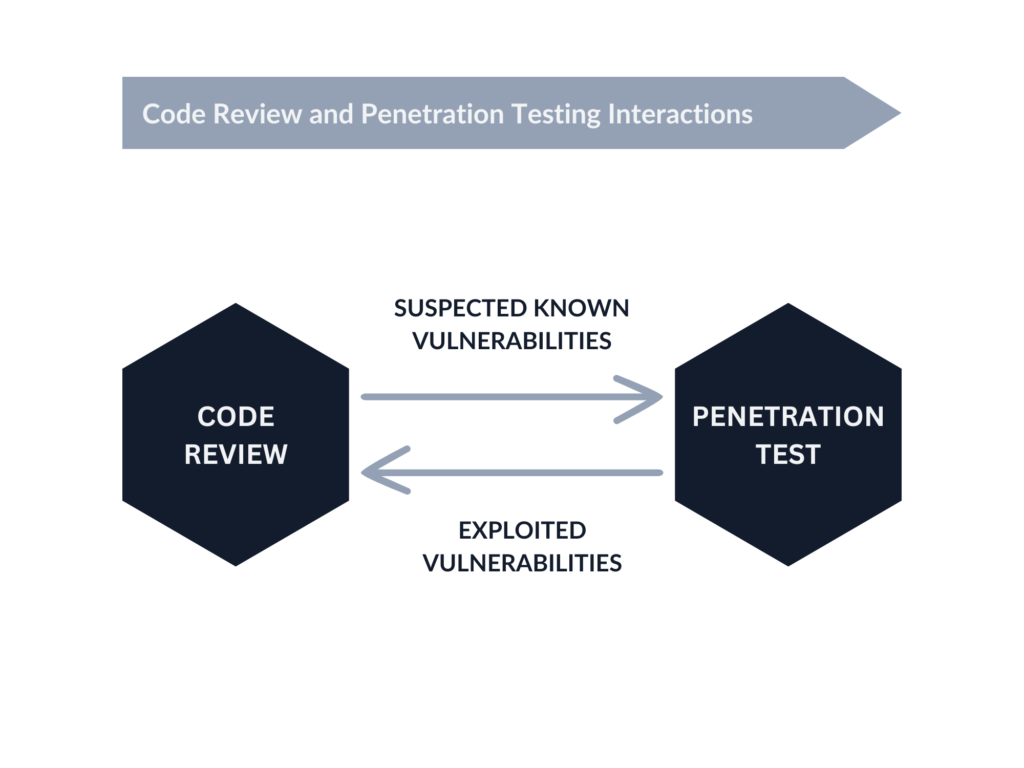
Security code review and penetration test synergy
Insight into code helps to build test cases. As a result, penetration tests become more productive because testing can focus more on suspected or known vulnerabilities. Knowing about the use of specific languages, libraries, and configuration options can help penetration testers craft more effective payloads. On the other hand, the ability to validate the alleged vulnerability identified in the source code, directly in the test environment, provides additional confirmation of its existence. Finally, the results of a penetration test can be used to look for additional places where the same vulnerability may be present.
No method – whether it’s manual, automated penetration testing, or security code review, guarantees the identification of all vulnerabilities. Mixing different testing methods is a manifestation of a defense-in-depth approach that significantly reduces the risk of missing important pieces.
Incorporating security code review into the penetration testing engagement will definitely be beneficial for organizations with frequent changes to their software. We especially recommend security code review for projects that have the potential of source code being leaked.
DORA compliance
Security code review contributes to compliance with DORA principles. It aligns with DORA’s core objective of fortifying software components.
How to get a quote for your project?
Book a call or write to us to get a quote for security code review. Each application is different. You will receive a set of questions that will help us estimate workload and needed skills, based on which we will prepare an offer. If needed, we will contact you to discuss your specific needs, application functionality, and a broader context to guarantee that the results of security testing will have the best possible value for you.