Testy bezpieczeństwa zarządzania dostępem i tożsamościami (IAM)

Zarządzanie dostępem i tożsamościami (IAM) zapewnia właściwym osobom właściwy dostęp do właściwych zasobów we właściwym czasie. Gdy IAM jest źle skonfigurowane, staje się najłatwiejszym sposobem na włamanie.
Testy bezpieczeństwa zarządzania dostępem i tożsamościami pomagają proaktywnie identyfikować i naprawiać słabe elementy kontroli dostępu, zanim zostaną one wykorzystane.
Nawiąż kontakt z ekspertką od IAM na LinkedIn!

Dlaczego bezpieczeństwo IAM jest ważne
Głównym celem testów bezpieczeństwa IAM jest ocena odporności mechanizmów zarządzania dostępem i tożsamościami na rzeczywiste scenariusze ataków.
Pomoże to Twojej organizacji:

Nasz raport będzie zawierał przejrzyste rekomendacje, które pomogą rozwiązać problemy. Możemy również pomóc zwiększyć świadomość i wzmocnić wiedzę zespołu w zakresie IAM poprzez specjalistyczne sesje i praktyczne wskazówki.
Testy bezpieczeństwa IAM to coś więcej niż zgodność. To kwestia odporności.
Co wchodzi w zakres?
Testy bezpieczeństwa IAM mogą być przeprowadzane samodzielnie lub być zintegrowane z kompleksową oceną bezpieczeństwa chmury lub aplikacji.
Zakres jest zawsze dostosowany do Twoich rozwiązań, priorytetów i wymagań biznesowych. Jeśli szukasz inspiracji, poniżej zamieściliśmy przykładowe obszary objęte oceną.
Testy bezpieczeństwa IAM dla aplikacji webowych

Ten rodzaj testów jest szczególnie korzystny w przypadku aplikacji multitenant typu Software-as-a-Service, które są często podatne na ataki związane z zarządzaniem dostępem i tożsamościami. Jest to również świetne rozwiązanie dla organizacji z niestandardowymi, heterogenicznymi architekturami IAM, które chcą ocenić i ulepszyć swoje komponenty webowe.
Testy bezpieczeństwa IAM dla przedsiębiorstw
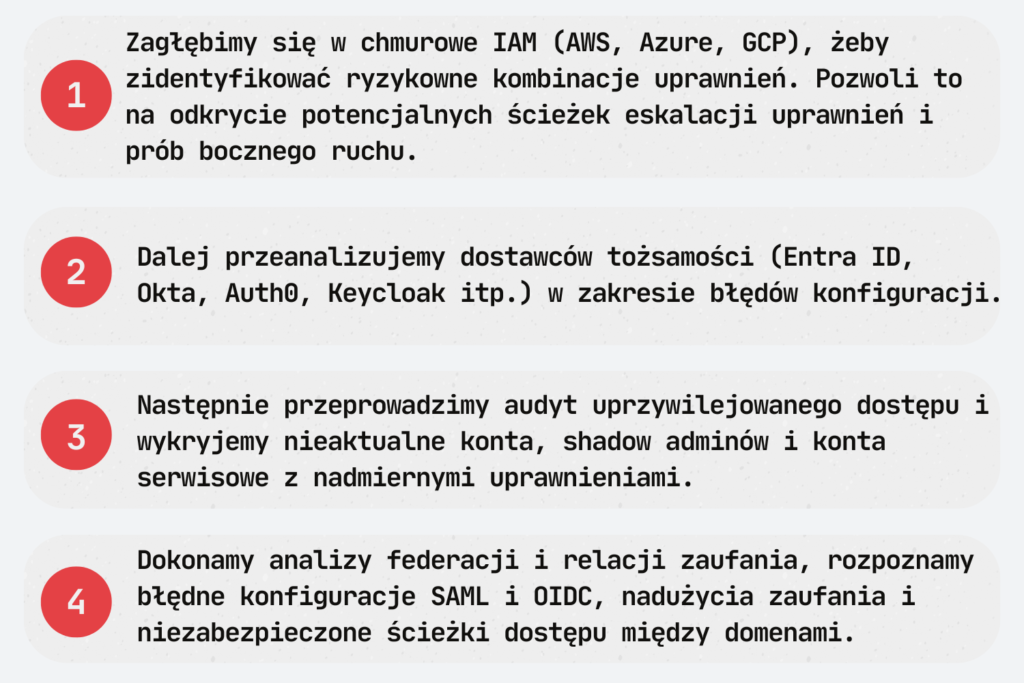
Dogłębna analiza architektury IAM przedsiębiorstwa obejmuje zarówno infrastrukturę chmury, dostawców tożsamości, jak i integracje aplikacji webowych. Aby zapewnić kompleksowy przegląd, weźmiemy również pod uwagę starsze systemy, które są nadal w użyciu, w tym wszelkie niestandardowe mechanizmy, na których się opierają.
Testowanie bezpieczeństwa IAM dla przedsiębiorstw jest najlepszym rozwiązaniem, jeśli szukasz jasnego zrozumienia swojego obecnego środowiska IAM i możliwych do podjęcia kroków w celu poprawy.

How it works
Nie ograniczamy się do skanowania. Naszym celem jest symulowanie prawdziwych atakujących, którzy nie polegają na szczęściu, ale na logice, wytrwałości i przeoczonych błędnych konfiguracjach.
Cechą wyróżniającą naszą usługę jest dogłębna wiedza, która się za nią kryje. Wyprzedzamy konkurencję, uważnie śledząc najnowsze techniki ataków wykorzystujących tożsamość, nadużycia IAM w chmurze, prawdziwe schematy włamań i przeprowadzając własne badania, które można znaleźć w naszej Bazie wiedzy. Nasze podejście opiera się na sposobie myślenia atakujących, co pozwala nam odkrywać zagrożenia, których tradycyjne oceny często nie dostrzegają.
Z łatwością radzimy sobie ze skomplikowanymi zadaniami, niezależnie od tego, czy jest to niestandardowe wdrożenie SSO, środowisko chmury hybrydowej, czy nowatorski dostawca tożsamości. Każde środowisko jest traktowane jako unikalne, a nasza metodologia jest dostosowana do architektury, profilu ryzyka i kontekstu biznesowego.
Nie jest to zadanie polegające na wypełnianiu checklisty. Jest to ocena oparta na wiedzy i informacji o zagrożeniach, mająca na celu ujawnienie sposobu, w jaki tożsamość może zostać wykorzystana jako wektor ataku i jak temu zapobiec.
Wynik? Jasny, priorytetowy plan działania pozwalający wzmocnić ochronę tożsamości.
Get a quote for your project
Zarezerwuj spotkanie z naszym specjalistą lub napisz do nas, aby uzyskać wycenę testów Active Directory. Nasi eksperci skontaktują się z Tobą jak najszybciej i przedstawią ofertę dopasowaną do Twoich potrzeb. Każda organizacja jest inna – skontaktujemy się z Tobą, aby określić specyfikę i szerszy kontekst testów bezpieczeństwa.