How to prepare an effective threat modeling session
Every threat modeling session requires thorough preparation. This article will help you create an effective session step by step.

TL;DR – general steps
Threat modeling sessions involve complex preparation. However, this doesn’t mean that their organization will always be difficult and unintelligible. For TM sessions to be easy to plan, you should follow these basic steps:
- Think of what you need to know about threat modeling sessions, your organization, and working processes in your company to organize a such a meeting.
- Think who should be invited to a threat modeling session and what domain knowledge they need to have.
- Don’t invite managers to threat modeling sessions since attendees may feel awkward or unsecure when expressing their concerns about company threats in front of their management.
- Think about how and to whom to send meeting invitations and what to include in them.
- Think of roles that you will need to have during a TM session and consider people who will be able to play each of them.
- Create a meeting agreement so that the attendees will know what to expect and how to behave.
A well-planned and well-conducted threat modeling session already constitutes 50% of your success. Scheduling productive and time-optimal meetings is an art that can be learned by following a few simple rules. By mastering this easy technique, you can go further and plan and conduct good threat modeling sessions based on good practices.
If you are at such a stage when you are wondering if threat modeling is really for you, make sure to read my article on why threat modeling is important.
Over the past few years, I’ve had the pleasure of building a culture of productive meetings, brainstorming, gathering, and analyzing information with several teams. I have huge experience of working with Developers, Administrators, DevOps, Product Owner, CTO, CFO, COO, and other people in an organization, and now, also with our clients from different cultures and nationalities. Thanks to this, I can write with full conviction – yes, it is possible to plan, conduct, and summarize a productive threat modeling meeting by combining good practices for meetings and techniques and knowledge in the field of threat modeling.
Remember that this is a big collection of good practices based on many years of experience, but you do not have to apply all of them at once. You can start implementing them step by step in order to achieve great results in the future.
In the article I assume that:
- we are considering two types of threat modeling sessions: for a project that is in the preparation phase and for a project that is already in production
- you are a member / leader of a development team or a security team in your organization
- here, I am not talking about the TM methodology, this topic requires a separate article
Organizing threat modeling session – the first steps
At the very beginning, when you think about planning a threat modeling session, it is helpful to:
- Specify goals of threat modeling and its scope.
- Familiarize yourself with the steps that will be followed during the session, such as defining the scope, identifying threats, analyzing risks and remediation strategies.
- Gather any relevant data and information that will be useful during the session, like threat intelligence reports or security assessments results.
What do you need to know to organize a threat modeling meeting?
Depending on the form of the meeting, you choose whether it will be a small meeting during a project or a larger meeting before a project starts. You should take into account the difficulty of conducting the meeting itself. If you have:
- experience in meetings facilitation,
- experience in meetings moderation,
- technical knowledge in the field of safety and security,
- domain knowledge
you can confidently become an organizer and a participant. Otherwise, ask an insider or a company experienced in organizing threat modeling sessions to support you during the preparation phase and conduct a threat modeling session with you.
Who should be invited to a threat modeling session
A threat modeling session is a meeting where a group of individuals, typically of various roles, comes together to identify and assess potential threats to an organization or a system. This is why you should invite only the right people, who are necessary for the meeting and who can contribute to achieving the desired outcome. Before the session, justify why you need their help.
When planning this meeting, think about people who will contribute needed knowledge about the session domain and can be helpful in achieving the goal. Whether your meetings are live or virtual, you need the right people of the right roles and with the right experience or knowledge to make threat modeling productive. The added value of having people with different viewpoints and experiences is the fact that it allows for more diverse perspectives and ideas, leading to better decisions and outcomes. Ensuring that all parties are included in the discussion leads to effective collaboration and sharing different perspectives.
As I mentioned before, even people of some unexpected roles may give a helping hand when it comes to threat modeling. Below, you will find some examples of knowledge that people from your organization may contribute to a threat modeling session:
- Security Experts: security knowledge
- Developers: knowledge about software, code complexity
- Architects: knowledge about system architecture and solutions
- DevOps: knowledge about automation and security of components at the software and infrastructure
- Admins: knowledge about infrastructure
- People from business: assessment of business threats and which of them are acceptable
- Product Owner: planning and prioritization of tasks in the product backlog
- Scrum Master: help in planning corrections/changes for the teams
Keep in mind, however, that this type of threat modeling session using almost all of the features listed here is difficult to carry out, so it’s fine if you don’t implement everything at once. It is better to conduct such sessions during a project development phase and during its initial phase. When domain knowledge is not yet established and not all decisions defining a given project have been made – the system is in the process of design. At this point, you can determine what threats are likely to happen and what steps should be taken to minimize their impact on the system being created.
In the next phase of software development, it is also worth performing threat modeling before implementing the system to ensure that architects and developers have taken into account all possible threats. In this way, security gaps can be identified and corrective actions can be taken before implementation.
Depending on your organization’s meeting culture, you may or may not need to invite everyone to the meeting. Basing on a well-defined goal, you should determine what competences and domain knowledge you need and who exactly can help you.
Implemented and working system
If you are analyzing an already existing system, I suggest that you first break it down into smaller elements. For each of them, take into account people who have domain knowledge for the component in question and organized a meeting in a smaller group. This will allow you to perform threat modeling quickly and productively for a given component, and a result of the session can be discussed at a team meeting together with the project leader.
Here, you can find an example:
If one of the components, separated from the overall system that had already been implemented is an SSO (an authentication method that allows users to securely authenticate across multiple applications), you should: – invite DevOps who knows the details of the solution implementation and also knows what features have been used to enhance security: MFA, Adaptive Authentication, Device Trust, IP Address Whitelisting, etc. – invite an Architect who was responsible for the design and implementation of the solution, e.g., on the side of the cloud – invite a Developer who has knowledge of the software and APIs and participated in the implementation process Counting with you, it will be four people that have full competencies covering the scope of the issue.
In the case of smaller meetings, as in the example above, you can play the role of an Organizer / Facilitator / Notetaker and invite people with domain knowledge about the selected component (Participants – Developers, DevOps, Admins, Security Expert).
Each meeting is a cost for an organization – remember that – because during a threat modeling session employers stop doing their regular work tasks. Having a smaller number of people at the meeting also means less preparation and organization. Anyways, I encourage you to conduct an experiment and invite different people with domain knowledge to your future TM sessions – each of them may contribute to your session in a new and unexpected way.
Inviting people of different roles from your organization to the threat modeling session is important in order to get the full picture and work out the best practices together. The participation of experts from different fields allows us to have consultation and support in the decision-making process.
In my opinion, you shouldn’t invite Managers or high-level Managers to threat modeling sessions
It all depends on the culture of your organization… but
In my opinion, high-level managers should not be invited to meetings about technical details, and among others, to a domain–specific threat modelling session. High-level managers may limit freedom of speech and prevent technical experts from sharing detailed information.
High-level managers often focus on higher levels of strategy and planning rather than technical details. Their presence at a meeting can lead other participants to making decisions that are not based on actual technical risks, but rather on policy or business objectives.
In addition, high-level managers are often busy with their duties and do not have time to understand the technical aspects of threat modeling in detail, as well as time to prepare for the meeting in advance. Their presence at the meeting could therefore be a waste of time and an unnecessary cost for an organization, rather than some help to the technical team.
But remember that there are exceptions to the rule!
Regardless of the culture of your organization, relationships between people and the way they communicate, consider that people may want to safeguard their thoughts and ideas. To ensure openness, activity, and communicativeness in a meeting, select people in such a way that will reduce distance in communication, both culturally and hierarchically (if you have one in your organization).
All the information discussed during a threat modeling session will be available in a report or a meeting summary anyway, and this type of procedure will help reduce the feeling of judgment/discomfort in others because of the presence of senior managers.
Think about it – I’ll leave the choice to you.
How to send a meeting invitation
For many of your coworkers, threat modeling may be a completely new experience and they will not know what to expect. In an invitation before the meeting, define its purpose clearly: make sure you personally and your coworkers understand what the meeting is about, why it is necessary and what you hope to achieve. Then, send out invitations and the agenda to all attendees and provide any necessary materials or information beforehand. It is a good thing to send attendees a reminder a few days before the meeting to make sure they will come prepared and will not forget about the threat modeling session.
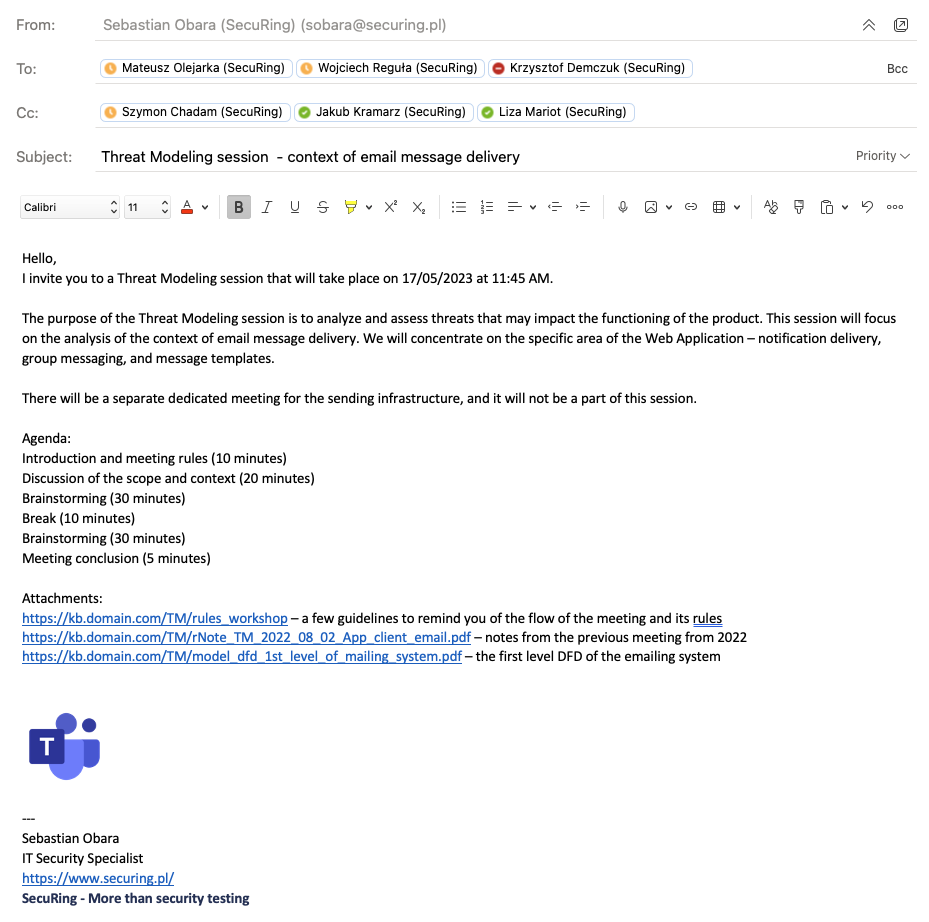
Organizational roles in a meeting
We have already determined who we want to invite to the meeting from the organization, so it’s time to go through assigning roles in the meeting. This is important if you don’t want to play all the roles in the meeting on your own, or if you’ve invited a lot of people and you’re concerned about the productivity of the meeting.
Roles: Organizer / Leader
The Organizer/Leader is a person who supervises the process, ensuring that a discussion or a meeting takes place in accordance with the established rules and agenda. They are responsible for organizing the meeting/creating idea.
Roles: Moderator
A person performing this role tries to maintain order during the discussion, ensure equal participation of all attendees, as well as prevent possible conflicts or manifestations of aggression. Moderation is especially useful for meetings with many participants and when a discussion is about controversial or emotional topics.
Role: Facilitator
The Facilitator’s main responsibility is to keep a conversation on track. The Facilitator plays a more active role in moderating a discussion and guiding the decision-making process.
Role: Notetaker
A person playing this role should record the key elements and progress of the meeting. They can use an additional whiteboard, sticky notes, photos, etc. This is a very important role that will allow you to return to this meeting after it is over and create a summary.
Role: Participant
A person invited by the Organizer/Leader. Has necessary technical/domain knowledge on the topics discussed at the meeting/session.
During smaller meetings, you can play the role of an Organizer / Facilitator / Notetaker at once and invite people with domain knowledge about the selected component (Participants – Developers, DevOps, Admins, Security Expert). Before a TM session, answer the question whether you need to invite other people to help you with these roles and whom to invite.
Meeting agreement
I think everyone would like to run their meetings smoothly. This is why, before a threat modeling session, you should always consider having a contract and a set of rules, so that the attendees know what you expect from them.
For this purpose, you should prepare a good meeting contract that will contain the following elements:
- Goal: clearly define the purpose of the meeting, including goals and objectives that you hope to achieve, make sure that everyone knows what the goal of the meeting is.
- Agenda: outline topics that will be covered during the meeting, along with expected outcomes and any necessary details or resources.
- Communication: specify how communication will be conducted during and after the meeting, including any necessary details about an email, a phone, or other communication channels.
- Materials: if necessary, specify any that apply to the meeting and information that will be shared.
- Breaks: allow taking breaks during long meetings to help attendees stay focused and energized.
By including these elements in a meeting contract, you can ensure that the meeting is productive and efficient and that its goals and expectations are clear to all the attendees.
Any rules that affect the possibility to conduct a productive meeting are good and you can confidently use them.
Summary
Let’s answer the main question of this article – how to prepare an effective threat modeling session? You already know that an effective threat modeling session is directly related to a well-prepared meeting, clearly defined roles, and people you invite. With this knowledge, conveyed in a nutshell, you can experiment with threat modeling sessions or other meetings on your own – I encourage you to do so!
Just remember that it is not necessary to implement all the good practices that are communicated here at once, every organization needs time for change, so give it this time and be patient.



