AppSec Europe 2018 – conference recap

AppSec Europe is the premier application security conference for European software developers and security experts. For many years we have been participating in subsequent editions of this conference, both as speakers and participants. This year it was no different.
Apart from our own presentations at Application Security Europe 2018 we were pleased to listen to others as well. Check out our recap of the conference, especially the Hacker track.
Passive Fingerprinting of HTTP/2 Clients (by Elad Shuster)
It was about the detection methods of the HTTP/2 libraries that connect to the server. Different implementations use unique values of some parameters and do not change the frequently. It is useful when you want to detect some bots that use single HTTP/2 client library.
Secure Messengers and Man in The Contacts: The Ultimate Spear Phishing Weaponi (by Laureline David and Jeremy Matos)
The main idea was to create malicious app that has access to your contacts (you actually give the permissions) and then all your contacts are drained to the malicious C&C. After that, the attacker knows exactly who do you have saved and using the malicious app is able to create a duplicate but with other phone number (the permission to contacts allows both to read and write to the contacts). Then, the attacker is able to send you a message via for instance Signal (from number that belongs to the duplicated contact) and you will be probably social engineered. The researchers reported this and they received following responses:
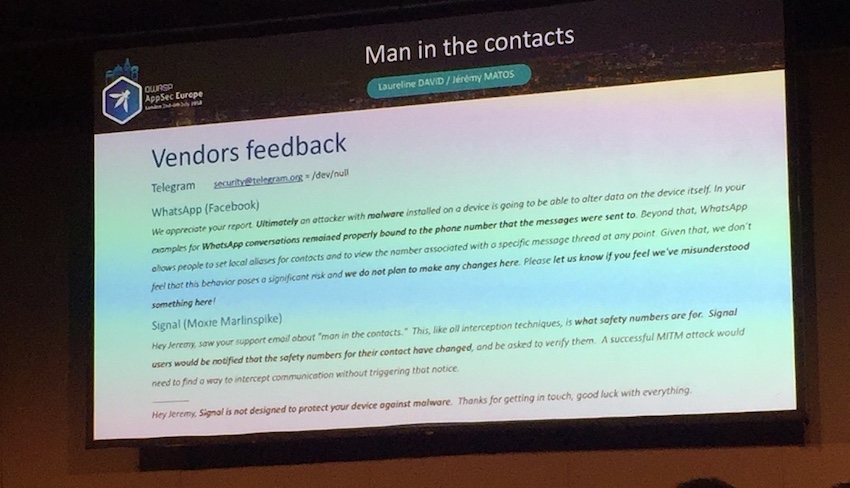
The Last XSS Defense Talk: Why XSS Defense has radically changed in the past 7 years (by Jim Manico).
Jim is Jim. The presentation was very addictive even though Jim was talking about mechanisms that are or should be very well-known already. Funny style with XSS payloads that send an email to your boss that he is a jerk – it might be exploit as well.
Damian Rusinek
Like every Jim’s talk – very dynamic, interesting and funny. Jim has amazing energy and loves to spread the knowledge. To pentesters I think the content was nothing new, but for people who are not aware how to deal with XSS’ – must to see! Jim, as a part of super cool OWASP community, is going to share the slides on CC license!
Wojciech Reguła
Double selfie with @manicode 😀 pic.twitter.com/VxljpT7qM1
— Damian Rusinek (@drdr_zz) July 6, 2018
Attacking Modern Web Technologies (by Frans Rosen)

One of the best talks IMO with many interesting attack scenarios. Frans started with showing how to exploit the AppCache to get access to “hidden” URLs. Then he showed how to bypass upload policies in the cloud and how to bypass SOP with postMessage.
Damian Rusinek
A lot of interesting examples that had a real impact on business models (for example how Dropbox was forced to delete users’ personal directories). Over 3,6 slides per minute – pretty dynamic presentation!
Wojciech Reguła
Prepare(): Introducing Novel Exploitation Techniques in Wordpress (by Robin Peraglie)

Prepare function is still a problem in Wordpress event though there are good replacements. This talk was about 2 interesting exploit scenarios that used prepare function as a vector.
Exploiting Unknown Browsers and Objects (by Gareth Heyes)
Very nice presentation about Hackability Inspector tool. It checks and performs some basic security checks on all JS objects available in the window. It is especially needed when you have no developer console available in the web browser.
Winning – the future perspective in the next 20 years! (by Andrew van der Stock)

One of our favorite talks. It was not technical and basically showed that Top10 like OWASP’s was already created in 70s. The takeaway was a thought that the security is mainly the problem of people and not applications and we, as security experts, should be a equal partner for a developer.
XSS is dead. We just don’t get it. (Mario Heiderich)

Mario touched the interesting problem – glorification of vulnerabilities instead of fixes. He also asked a question who really wants the XSS to be permanently fixed – the king of every bug bounty program!
Seconds out! When algorithms don’t play nice with our applications and lives (by Etienne Greeff)
This talk was about machine learning and AI and it was about a specific problem which is crucial in ML. Etienne showed the results of his research where he tried to find the domains used as C&C domains. He pointed out practical examples on the type of problems AI & ML can solve and stated that we need ML and AI in cybersecurity world.
Finally, we would like to quote a few opinions about our presentations which were particularly well received. Both topics that we presented were included in the Hacker track. Thank you!
Testing iOS Apps without Jailbreak in 2018 – Wojciech Reguła

- Click and read the presentation
- Please find also a write-up that summarizes a pratical part of the presentation
Outsmarting smart contracts – an essential walkthrough a blockchain security minefields – Damian Rusinek

- Click and read the presentation
- Download our handbook How to Develop Secure Blockchain Applications
Head of Blockchain Security



