Local Privilege Escalation in macOS infrastructure
In this article we present you a common vulnerability pattern that we observe in Mac infrastructures. Elevating privileges on one machine may allow the attacker to compromise all Macs in the company.

MacOS infrastructure
Apple devices have been present in the companies for a long time. Wherever there is a need to deploy iOS applications, testers and programmers have to use Macs. UX/UI designers and movie editors use Macs for apps that have only Apple versions. It is also worth noting that Macs are introduced to companies as the managers and directors want to use them as well. While Windows infrastructure in big companies is usually mature and well-tested, Macs infrastructure is usually no man’s land. After digging in some huge networks we observed a lot of ugly hacks and bad scripting exposing the company’s security. Compromising one Mac can have influence on the whole intranet as they have often access to SMB shares, do Kerberos authentication to the internal resources.
Vulnerable pattern
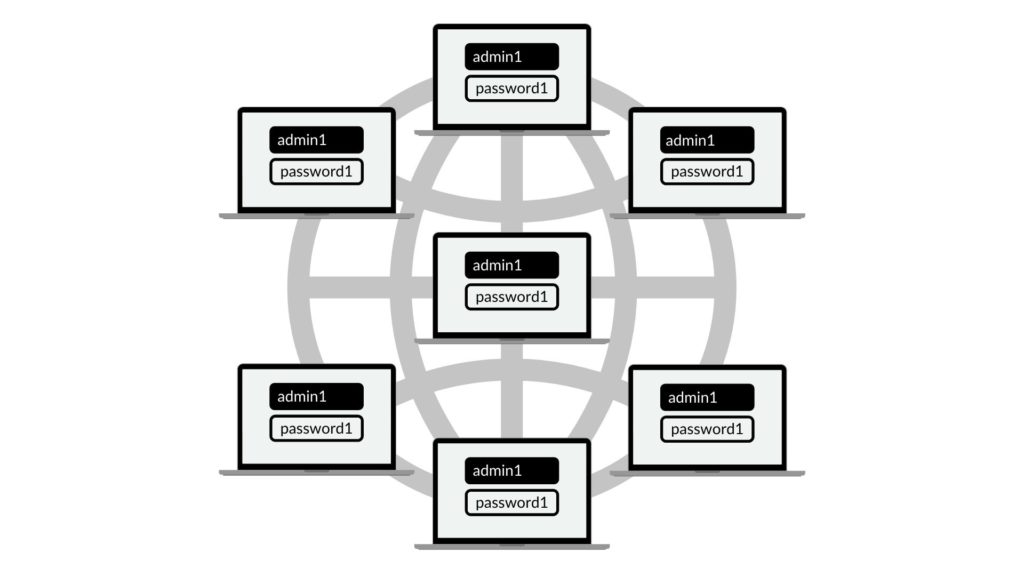
In this article we’d like to show you a common, vulnerable pattern present in macOS networks. Machines need to be somehow managed. The most efficient way nowadays are hybrid solutions that both enroll devices to the MDM and install agents. The MDM profiles are nice but have limitations, so for the wider management functionalities, systems employ traditional SSH connections. The problem starts when macadmins use the same account with the same password across all devices in the network.
Elevating privileges on XPC vulnerabilities example
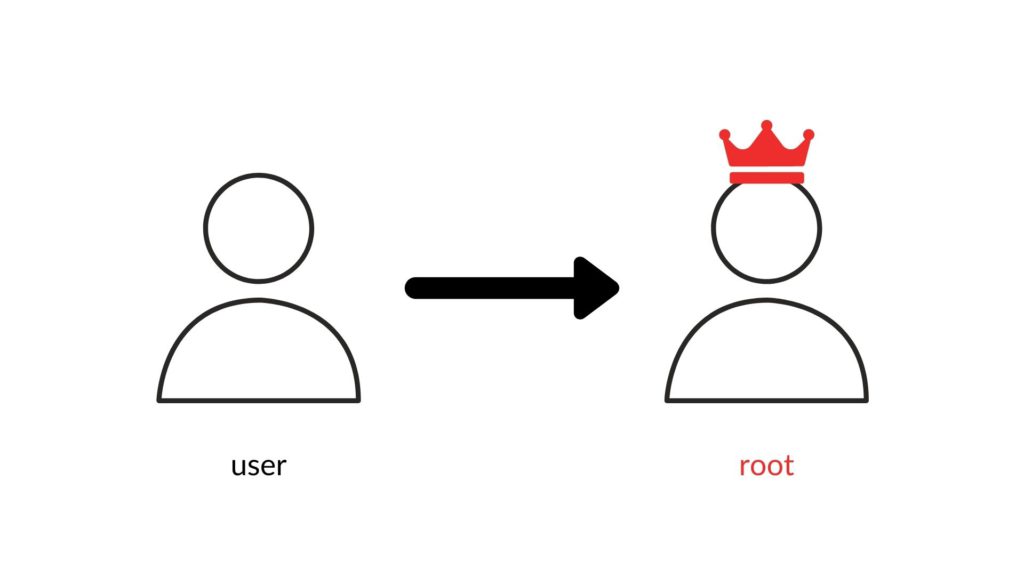
Typically in the managed Mac infrastructures users do not have root privileges. They run on standard users that are not in the admin group and are not included in the sudoers file. Attacker who compromises one machine, usually wants to perform a lateral movement and compromise other Macs. If the network implements the above-mentioned vulnerable pattern, the easiest way is to elevate permissions from the user to root and steal the macadmin’s password via a fake SSH server.Recently, one of our security consultants had a talk about “Abusing & Securing XPC applications”. Using XPC to elevate user’s privileges seems to be a perfect solution for that purpose. As shown in the presentation, the XPC vulnerabilities are everywhere. If you are interested in XPC exploitation, we strongly recommend watching This talk.
Lateral movement
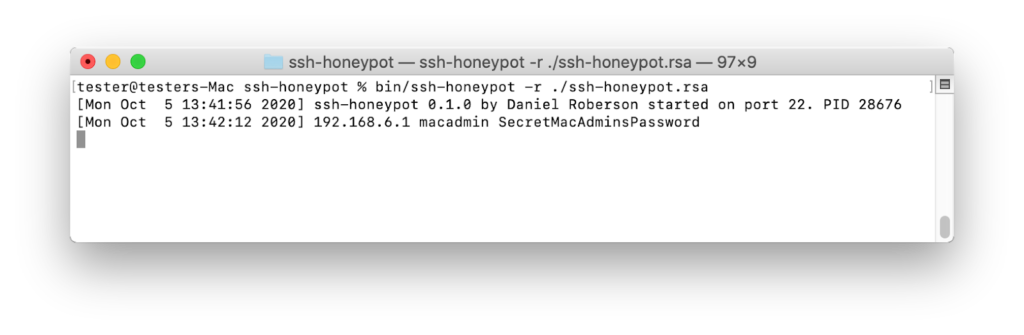
To fake the SSH server, we can simply use the SSH-Honeypot project. Clone it and run the following commands:
#!/bin/sh
brew install libssh json-c
make -f MakefileOSX
bin/ssh-honeypot -r ./ssh-honeypot.rsaNow wait until the macadmin connects to the SSH:
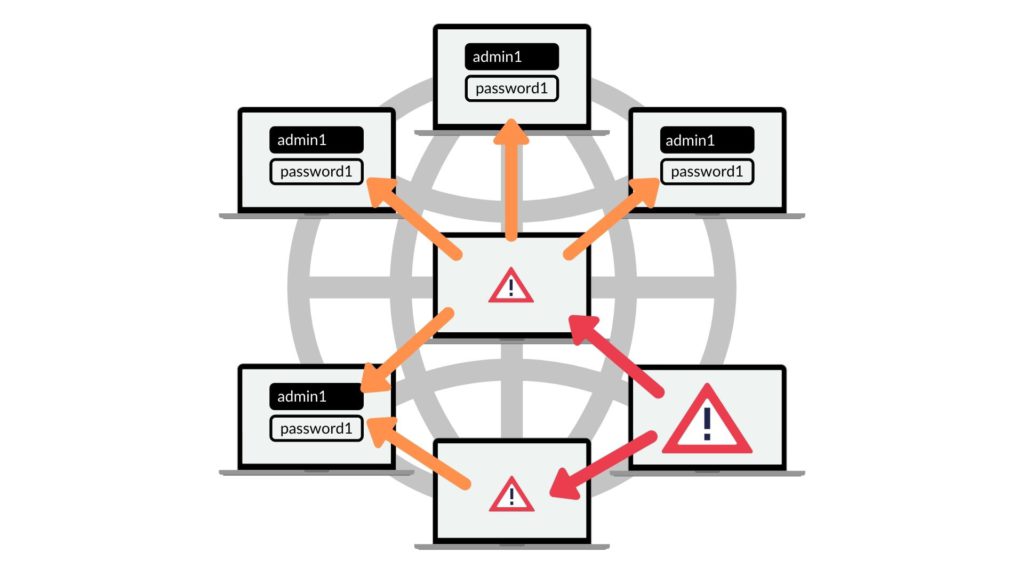
Now, we can perform lateral movement to compromise other machines.
Summary
In this article we wanted to present you a common vulnerability pattern that we observe in Mac infrastructures. Elevating privileges on one machine may allow the attacker to compromise all Macs in the company and thus access sensitive resources available from each machine. Vulnerabilities in applications are not rare, so in professional networks remember about logging and incident response solutions. Keep in mind that responding to incidents is a defense-in-depth practice and every large Macs network should be thoroughly tested. Infrastructure assessment allows detecting such vulnerable patterns and making your network more secure.
If you want to secure your infrastructure leave your contact details in our form. We will get back to you to discuss your case as soon as possible.
Head of Mobile Security



