Hackflix & Skill – Security Series for developers
Hackflix & Skill is a TV-series-like security course in which Buggy will guide you through the most common vulnerabilities, such as XML External Entity Attack, Privilege Escalation, Cross-Site Scripting, SQL Injection, Remote Code Execution, and many more… All of which we encounter during real-world security tests.
Training has various applications thanks to the different approaches to security awareness. It may be used:
- As a part of the developers’ onboarding program,
- To promote security knowledge outside the security department,
- For effective technical training at scale according to current best practices in application security,
- As a building block for a security awareness program in your organization.
It is a fun alternative to one-shot security workshops that will help you make sure every participant is involved on a bigger scale.
What does this security course look like?
The program is based on a TV series formula. There are 5 modules – we call them episodes. Each episode has its own story based on real-life cases of security issues that we have encountered in our daily work.

Where is the plot twist? – You control the plot.
The students are involved in a dialogue with the character and solve exercises and quizzes to consolidate newly acquired knowledge. An interactive form of training allows for an engaging and modern way of consuming knowledge.

We will introduce your team to the hackers’ perspective, which will help them spot code weaknesses and significantly improve the security of the company and its products.
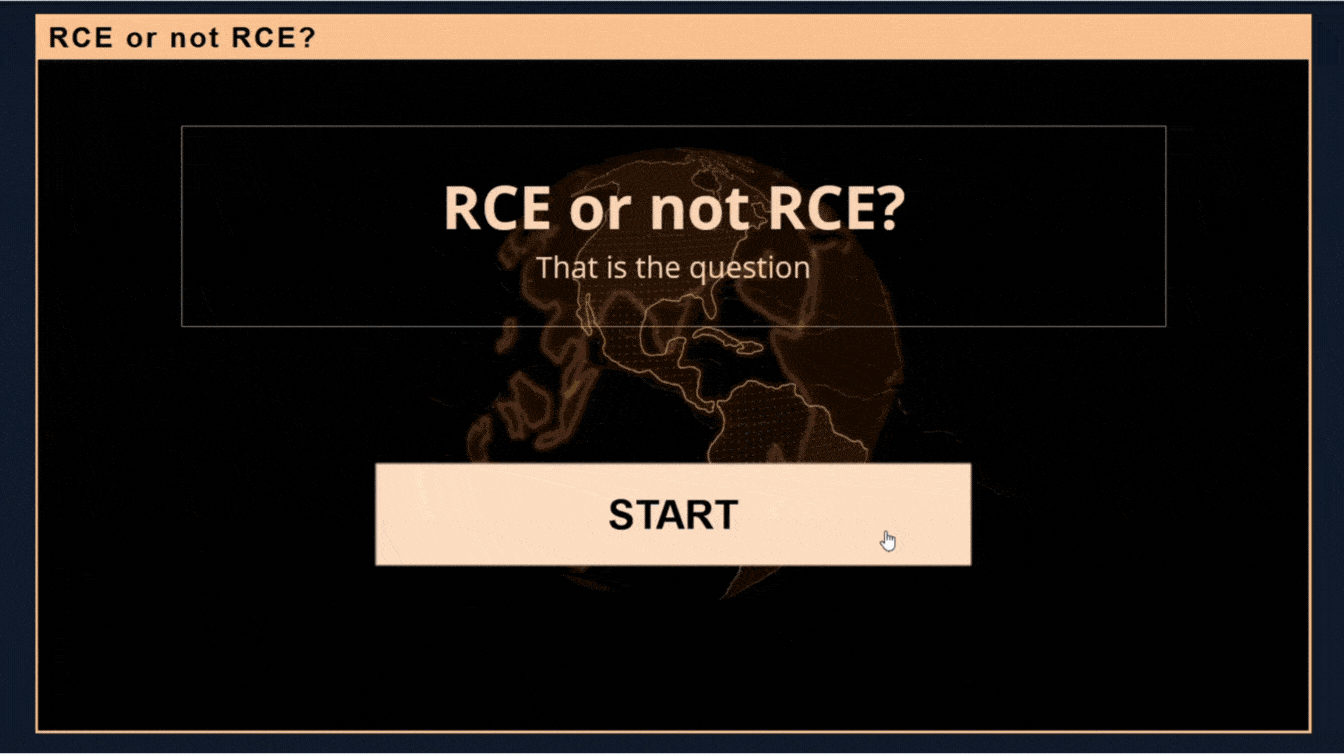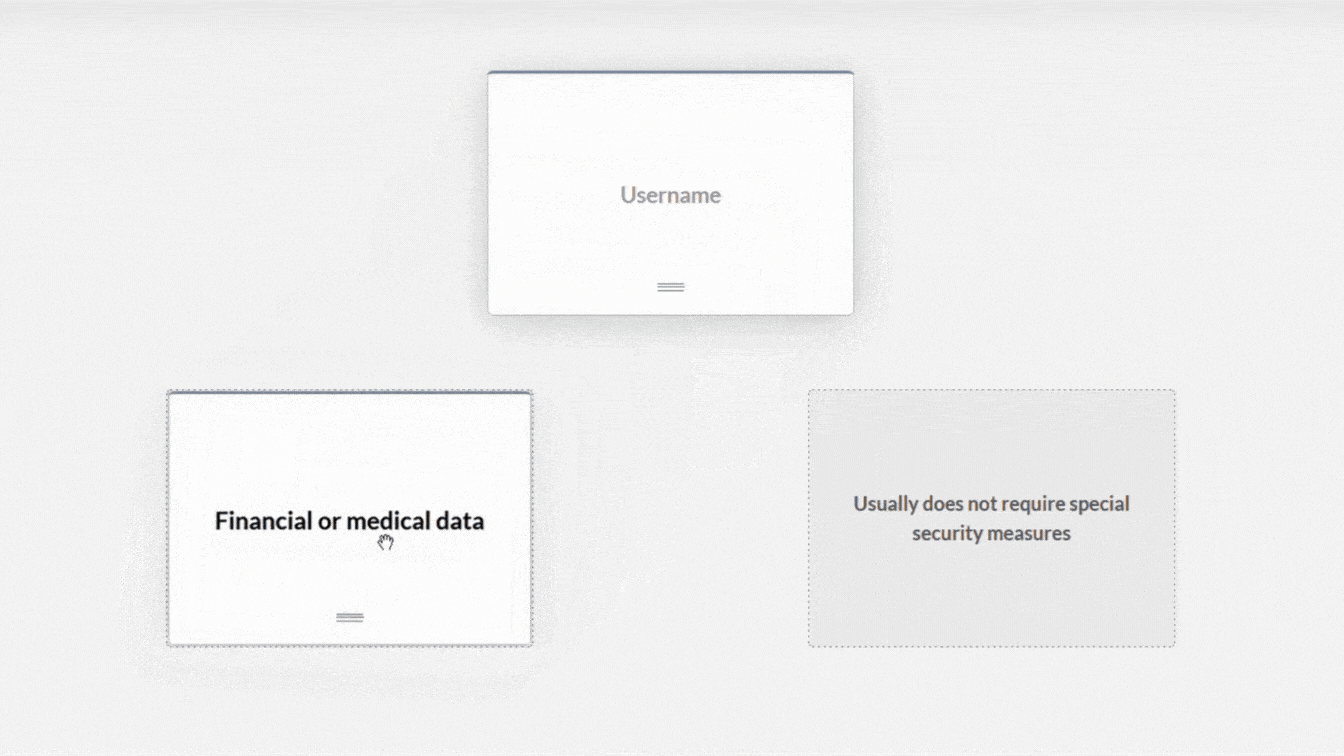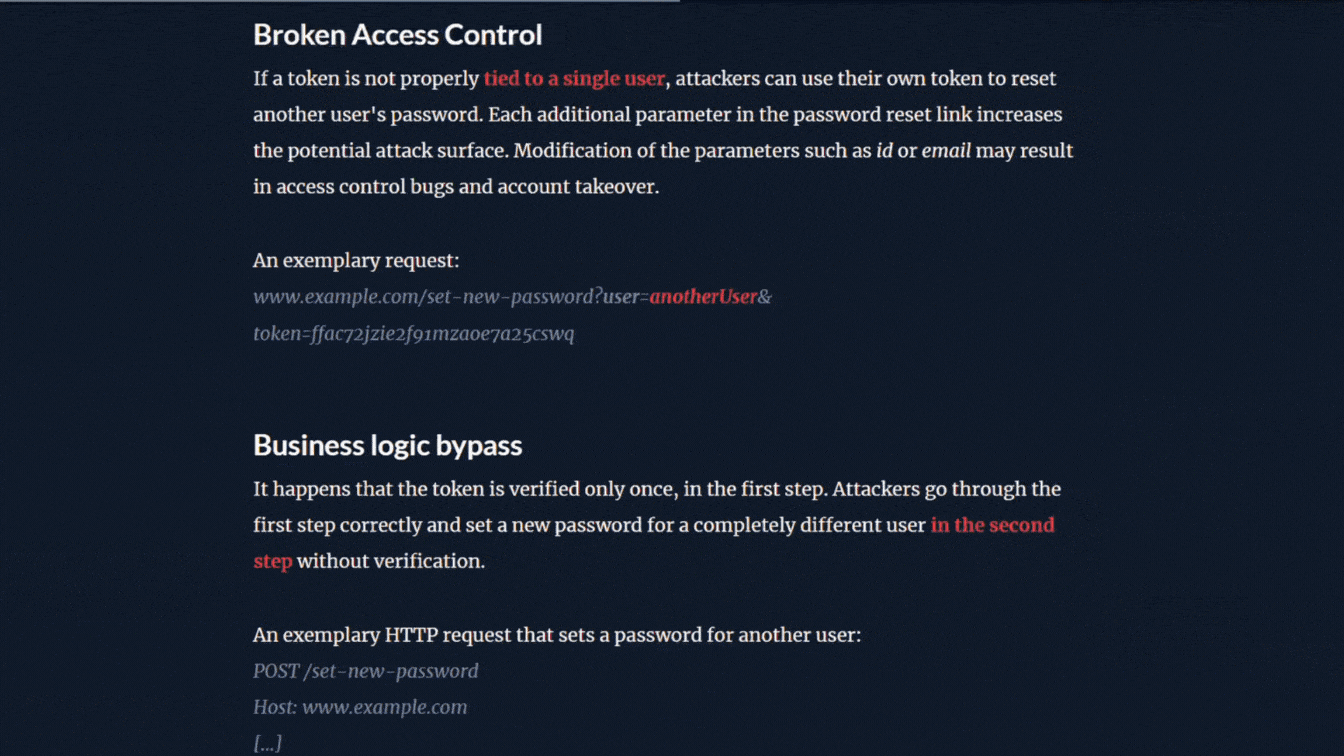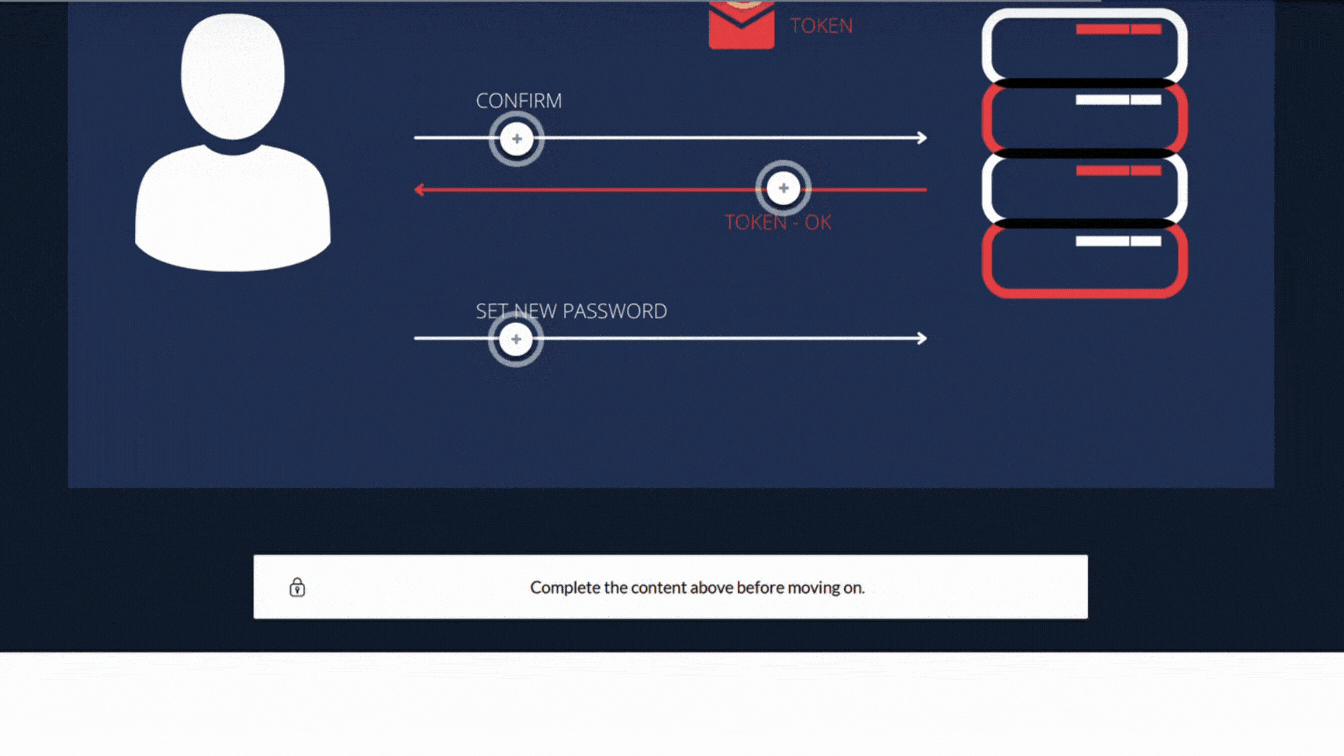
There is room for learning and making mistakes in the exercises that Buggy guides you through. Each exercise includes an explanation why that particular solution is a best practice.
Security content tailored for software engineers
The number of topics discussed in the training is really wide. We focused on comprehensive coverage of the most important security aspects while maintaining universality in relation to programming languages and selected technologies.

Each episode contains:
- A showcase of the best practices based on the OWASP TOP 10. We have selected examples that often appear in applications we test.
- Vulnerability chains based on real penetration tests (kill chains) that we had experience with during over 20 years of providing security services all over the globe
- Exercises with answers containing good and bad code examples, and the participant has to choose the correct one (based on real-world solutions)
- Multiple choice questions and quizzes at the end of each episode summarizing the acquired knowledge
- Threat modeling session on problem solving that will be the best fit for your organization
Hackflix & Skill is available for teams starting from 30 members
To make sure everyone is keeping up with the material, Hackflix & Skill course can be accessed through the special learning management platform. You can enroll users as well as track their progress.
If your organization already has its own eLearning software, you can get Hackflix & Skill as an exported SCORM package for internal use in accordance with your policy.
Using different formats? We also support AICC, xAPI, and cmi5 to cover the most popular LMS platforms on the market.
Bonus materials for developers that last
We also conducted research among developers during many cybersecurity conferences we attended. Based on their needs, we have created handy materials for everyday use:
- Buggy’s 1010 – a set of short and useful tips for developers based on the most common security bugs found in all reports – it helps eliminate the biggest security bugs right at the beginning of the SDLC.
- Security Reference – a document containing enhanced references related to the 14 categories in the OWASP Application Security Verification Standard 4.0 – carefully selected source of proven and reliable information.
Pricing:

If you want to get a more extensive introduction to our training, feel free to book a call with us or simply leave a message – we will get back to you and tell you more about implementing security into your organization.



